Anatomy of a Ransomware Attack
Because ransomware attacks appear to happen in real time, it’s easy to imagine that they are the result of a sudden and very rapid breach of your network defences – almost like a high speed missile that moves too fast for your safeguards to kick into place. When a global shipping company was hit by NotPetya virus in 2017, one IT administrator described how “I saw a wave of screens turning black. Black, black, black. Black black black black black.” Technical staff literally ran through the building, even into meeting and conference rooms, urging colleagues to unplug and disconnect their systems.
But while some ransomware attacks may indeed happen opportunistically, the majority of sophisticated and large-scale security breaches are the result of careful planning over an extended period of time.
The potential rewards of successfully targeting a larger company or Enterprise means that these advanced cyberattacks are methodical in their nature and can be analysed in process terms. So analysing the anatomy of a ransomware attack may help you review your safeguards and build more secure defences.
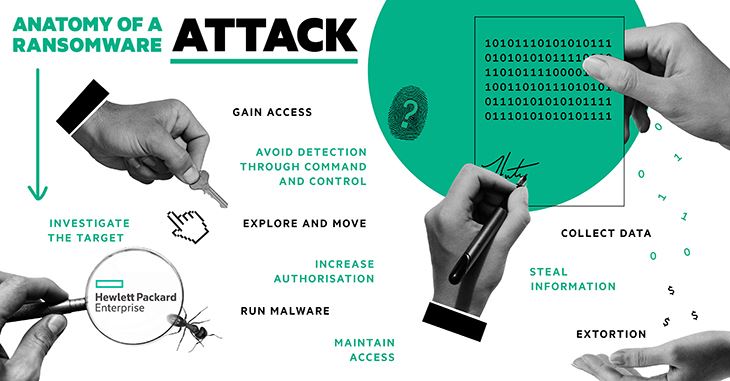
1. INVESTIGATE THE TARGET
The first stage of a ransomware attack is gathering OSINT, which stands for Open Source Intelligence. The internet is an ocean of data. OSINT can be in various forms like audio, video, image, text, files and tools like Maltego, Shodan and Kali can help criminals harvest information on network configurations, devices, email accounts and users. The objective is to build up an overview of an organisation and the individuals within it to probe for weaknesses and vulnerabilities. This is particularly useful for planning targeted spear phishing attacks that may be trying to gain higher level network access credentials.
2. GAIN ACCESS
When the time comes, the criminals will attempt to gain access to your network. As just mentioned, spear phishing is increasingly a common approach and could exploit the knowledge that a hacker has obtained about relationships between colleagues, suppliers and customers – e.g. an email apparently from a trusted source that contains a link to a malicious website or an attachment that can execute code. Another tactic may be to target a computer or device that OSINT has identified may be vulnerable due to out of data software or patches. This could be achieved by exploiting a remote code execution vulnerability to run shell code directly in memory (e.g. SMB EternalBlue and WannaCry).
3. EXPLORE AND MOVE
Once the attackers have gained a foothold, they may not immediately trigger the ransomware attack. Instead, they may try to move laterally through the network to quickly find other computers, especially backups, that they can infect and bring into their control. They can use system commands like ‘systeminfo’ or ‘net view’ to profile the host environment. Thieves know that if primary systems are taken offline, companies will resort to their backups. One tactic is to simply encrypt the backups – effectively “burning the lifeboats”. Another is to linger long enough for malware to infect all backup copies, trapping the target in a so-called “attack loop” where attempts to restore the backup data simply triggers the ransomware again.
4. RUN MALWARE
In parallel with this lateral movement, cybercriminals may run malware programs and scripts silently in preparation for their final attack, using command and control interfaces like PowerShell. It’s worth pointing out that the attacks don’t necessarily need to install a malicious file but could be manifested as a ‘fileless’ attack which stores a malicious script in the Windows registry.
5. AVOID DETECTION THROUGH COMMAND AND CONTROL
Throughout this period, there is a delicate balance to be struck between wanting to gain maximum control over the target infrastructure versus the risk of discovery. The longer and more persistent the intrusion, the greater the likelihood that the IT organisation will notice that something is wrong. Thieves may use multiple proxies to limit their traceability and try to blend in with conventional network traffic, using standard protocols like HTTP, HTTPS or DNS, and common ports like TCP:80/443 (for HTTP/S) or TCP/UDP:53 (in the case of DNS). Remote access tools, like LogMeIn, may be seen as legitimate tech support programs and be whitelisted by the host network. These can be used to spread Trojan horses, like Backdoor.Jiripbot, that can open back doors on other compromised systems. But although some cybercriminals can lurk inside a network for some time, building their influence, generally, there is an imperative to launch the attack sooner rather than later. With careful planning – as in the case of the global shipping company mentioned in the introduction and countless other high profile attacks – the impact can be truly devastating.
6. INCREASE AUTHORISATION
While this is happening, cybercriminals will also be focused on increasing their control through privilege escalation. Privilege escalation means using some bug, design flaw or loose configuration in an operating system or application to gain higher access to resources that are normally unavailable to an application or typical user. The attacker can then use these newly gained credentials to run powerful administration commands; deploy password dumping tools like Mimikatz to obtain other credentials; stop anti-virus and other security services; and install additional malware that can wreak havoc on operating systems, server applications and day-to-day user operations. Worse still, malicious admin users can hide their tracks by deleting access logs and other evidence which can leave the victim unaware of what is happening.
7. MAINTAIN ACCESS
Throughout the attack, criminals may use specific tactics to ensure that they can maintain access to systems despite restarts, password changes or any other configuration changes that could sever their intrusion. Such scripts can also extend their network explorations. Attackers with sufficient admin rights may create a local system, domain or user that does not require them to use remote access tools. They might also create a new VM under their control to run their malware. Recently cybersecurity specialists, Sophos, identified that the gang behind Ragnar Locker virus used a Windows XP VM to run the program (and a copy of Oracle VirtualBox to run that). This so-called ‘living off the land’ tactic entails using legitimate software administration tools that either already exist on the network or that don’t look suspicious or out of place (e.g. PowerShell, TeamViewer). The safeguards that isolate hostile guests from hosts in a virtualised environment were ineffective here because the attackers had access to both the guest and the host.
8. COLLECT DATA
Ultimately, one of the reasons ransomware is so effective is because it targets the lifeblood of an organisation: its data. Thieves can use their privileged access to collect and copy data; eavesdrop using webcams and microphones; run keylogging and screen capture programs; mine code repositories for intellectual property; remove backup files; target email accounts to collect more sensitive information. All of this material has a high potential value in terms of dollar or reputational cost.
9. STEAL INFORMATION
With this privileged access, thieves can encrypt your data so you can no longer access it or compress and exfiltrate (copy and remove offsite to a remote server). Big movements of data can trigger warnings so thieves are careful to separate data payloads into smaller packets to avoid unusual data transfers, possibly using different networks like WiFi, 4G or Bluetooth.
10. EXTORTION
One of the most disturbing recent trends in the development of ransomware threats has been thieves threatening to publicly share information to extort their victims to pay. In April, the group behind Ragnar Locker attacked the network of Energias de Portugal (EDP) and claimed to have stolen 10 TB of company data, demanding a payment of 1,580 Bitcoin (approximately $11 million US) and threatening to release the data if the ransom was not paid.
Ransomware is a multi-billion-dollar industry, offering enormous rewards for its participants, so it’s perhaps not unsurprising that the leading exponents plan their exploits with the same care and precision that enterprises plan new product introductions and other projects. The anatomy of a ransomware attack is sophisticated and it is challenging for companies to maintain perfect security 24 x 7 x 365. Building up a circular ring of defences, with different solutions and safeguards, is the best way to ensure that in the event of a ransomware attack, you have options even if one barrier or wall is breached. In particular, maintaining copies of all your mission critical servers, domain controllers, databases, application and user files on an offline medium like LTO tape, is a critical safety net to maintain a recovery path and access to data in the event that criminals manage to take over your entire IT environment, including disk or cloud-based backups.